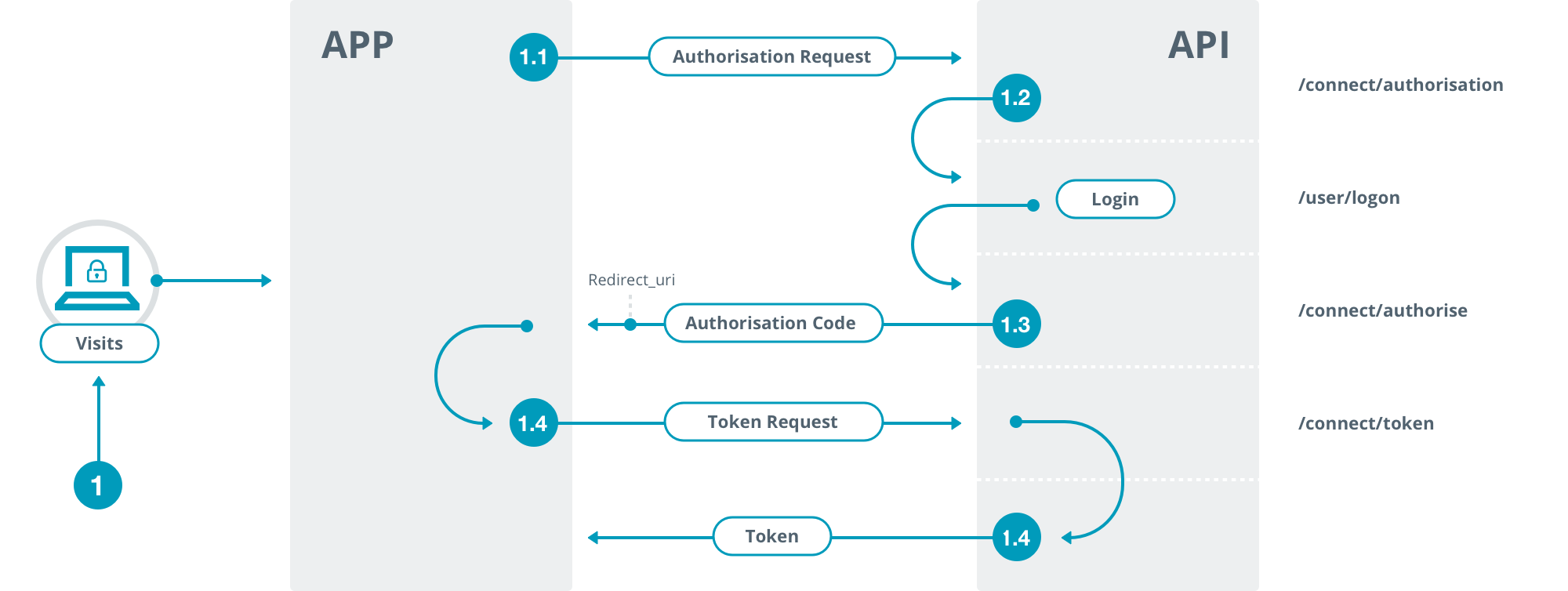
We recommend the use of this OIDC flow for most server-based clients, browser-based clients and mobile applications.
1.1 Client issues authentication request
Redirect the user-agent to https://exampleapi.mmcnz.co.nz/connect/authorize, providing the following parameters in the query string:
- client_id = your client_id
- redirect_uri = your pre-registered redirect_uri
- response_type = "code"
- state = a randomly generated nonce
- optional) scope = "openid"
It is important that both the client_id and redirect_uri match the pre-registered values obtained during registration.
The state parameter is a random string which you should keep (common practice is to store it in a cookie), and use later in step 1.3 to validate that the received authorization code was in response to the same request.
The scope parameter is used for standards compliance, and is also used in some of our more complex scenarios to select which user to generate a token for. It is not required to obtain a normal investor's authorization token and is treated as if it were "openid" if omitted.
1.2 Apex NZ Registry API authenticates user
The Apex NZ Registry API will now authenticate the end-user. This will usually involve a log-in form, with username and password. If the user successfully completes this step, flow continues to step 1.3
1.3 Apex NZ Registry API issues authorization code
The Apex NZ Registry API will now redirect the user-agent to the redirect_uri provided in step 1.1
This request will contain the following query parameters:
- code = authorization code
- state = state parameter from 1.1
It is important that the client validate that the state parameter matches the value provided in 1.1. This prevents a class of attacks where the client application is tricked into attempting to obtain an access token for a user other than the one currently using it.
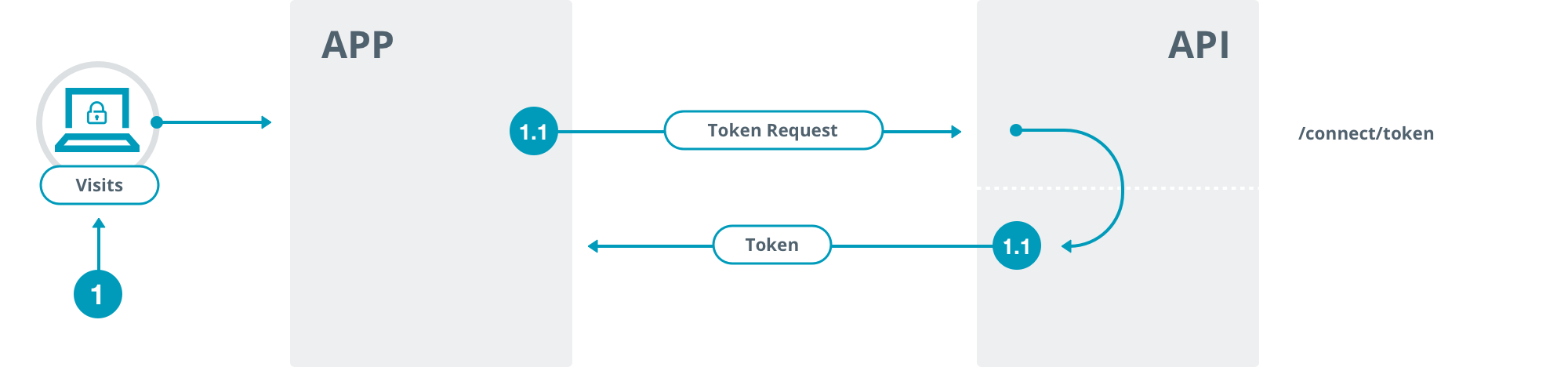
1.4 Client makes a token request to exchange authorization code for token
The client application makes a request using HTTP POST to the token endpoint https://exampleapi.mmcnz.co.nz/connect/token providing the following form (application/x-www-form-urlencoded) parameters:
- client_id = your client_id
- redirect_uri = your pre-registered redirect_uri
- code = authorization code from step 1.3
- grant_type = "authorization_code
- (server applications only) client_secret = your client_secret
Browser applications and mobile applications which are not able to keep a confidential secret should not use the client_secret parameter.
A successful exchange response is a json document. The example below omits some keys you will observe in a real response, but these can be ignored.
{
token_type: Bearer
access_token: 'access token string'>
expires_in: integer
id_token: 'id token string'
}
The access_token can be used to access the API. The access token will consist only of characters which are valid in a base-64 encoded string, but is not valid base-64, and should not be decoded or otherwise transformed.
The id_token can be used if you wish to use the userinfo endpoint, but can otherwise be ignored. The id_token is also a JWT, and can be decoded using the keys found at https://exampleapi.mmcnz.co.nz/.well-known/jwks
expires_in is an integer number of seconds, after which time the access token will expire.