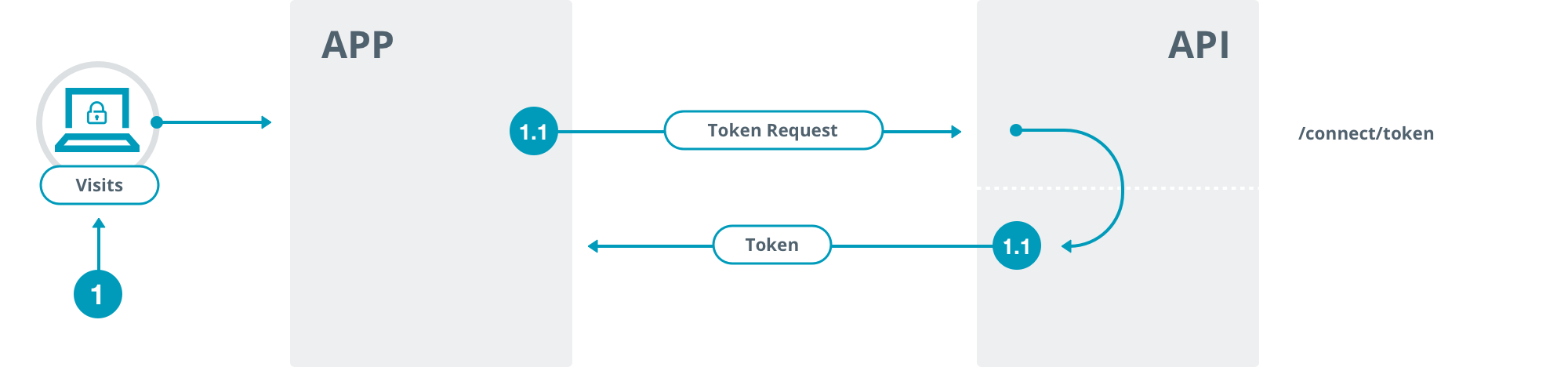
To provide a secure environment across all Apex NZ’s systems and services, the user accessing the system first needs to authenticate themselves via a username and password combination.
We use the OpenID Connect / OAuth 2 protocol and host (via the API) a series webpages that manage login and user creation process (including password reset and email workflows).